There is much brouhaha and kerfuffle at the moment about the fact that malware for the Mac has finally arrived in strength. I’m not sure why anybody is surprised; we knew this day would come and, more importantly, we knew it probably wouldn’t be as bad as things were for Windows users in the days before XP SP2.
(tl;dr: here’s what you can do to avoid or cure the problem.)
Out of a sense of duty to the Mac user community – well, more accurately, because I was looking for a way to avoid working on anything useful – I took it upon myself to locate one of these pieces of malware and have a look at what was going on. It didn’t take long to find a link to a site hosting Mac malware posted in the Apple support forums (which, in turn, I found via the ClamXav forums), and I was able to get procrastinating.
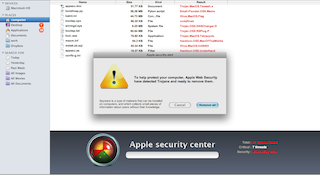
The page I went to (which I will not link to, obviously) presented me with a screen that made a rather pathetic attempt to look like a Finder window, and displayed an animation that looked like it was performing a virus scan; this is what it looked like once the not-actually-a-scan was finished (n.b. these screenshots are links to the full-size version):
There was one thing very obviously wrong about this: it used the font Arial, rather than Lucida Grande which is the default Mac system font. Given Arial’s total lack of resemblance to Lucida Grande, this meant it looked like pants.
In addition, the left column did not reflect reality: the name of the hard drive was the default “Macintosh HD”, and the list of folders below that was not the list I have. (I see however that Dropbox is now so popular that it found its way in there… or maybe this reflects the machine of the person who created this thing.)
And, of course, there’s the lousy grammar in the pretend dialog box.
In fact, this page was nothing but HTML, CSS and JavaScript. However, in addition to showing off this fancy animation, it also downloaded a file called “anti-malware.zip”. In fact, it downloaded this as soon as the page loaded; the animated “scan” merely served as a distraction from this activity, although in my case the payload had completed downloading before the “scan” was even 32% complete. A bit sloppy IMHO – it should have made a song and dance about performing the download after the scan was complete.
However, one important point is that I have disabled automatic running of downloads in Safari. In a default configuration, this file would have been unzipped and its contents executed automatically. (See below for details of how to disable this.)
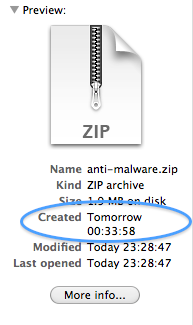
One further point to note was that the payload was apparently delivered from the future:
Subsequent visits to the site have resulted in files dating between around one hour and five hours in the future; this could reflect the file being hosted in a number of different places around the world and having the date it was uploaded to the server from which it happens to be downloaded, but could also imply that the file is being modified in an attempt to avoid detection by Mac anti-malware applications such as ClamXav.
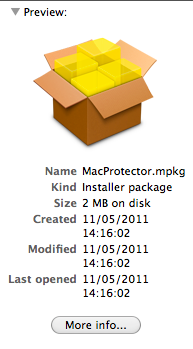
Upon unzipping this file, a Mac installer package was revealed:
Odd points to note: the creation/modification/last opened dates of 11 May 2011 are eight days before I downloaded this, which might mean that was in fact the last time the file was modified. This would suggest that the varying creation dates of my multiple copies of the payload reflect redistribution to different servers rather than modification of the software.
Anyway, an installer is no fun unless you run it, so here goes:
It turns out that the variant I’ve snared here is Mac Protector, which is interesting, as the forum link I originally followed said it was to Mac Defender, the other piece of malware that has been going around. The fact that a site that was serving one of them has switched to serving the other might be construed as implying that they are both under the control of the same entity, although it does not actually prove that.
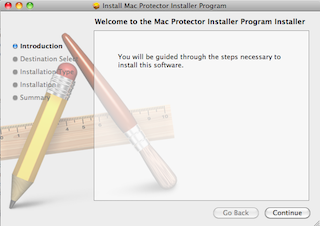
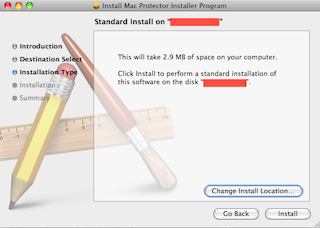
What we have is a standard Mac installer; so standard that they haven’t even bothered to create their own artwork to go in the background. The heading “Welcome to the Mac Protector Installer Program installer” is also sloppily constructed – it should just read “Welcome to the Mac Protector installer”.
I’ll click “Continue” so you don’t have to:
The installer has skipped the installation disk selection screen (although this is available via the “Change Install Location…” button), and gone straight to wanting to install on the main hard disk in my MacBook; it will require 2.9 MB of space.
Let’s click “Install” – but only after bringing up Activity Monitor and carefully positioning it next to that window, with the installer app selected so that I can hit “Force Quit” quickly if my gamble doesn’t pay off:
Phew, it was the red wire 🙂
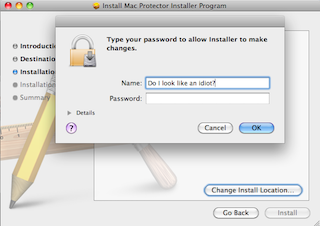
I was quite relieved, and reassured, to see the password prompt: clearly this thing cannot do any harm unless explicitly allowed to. The real problem is that Mac users have not yet been educated to beware of this kind of thing.
I stopped here, for obvious reasons 😉
tl;dr. So what do I do about it?
The first thing Mac users can do to protect themselves is to disable automatic execution of downloads by Safari. (People have been telling Apple this for years, but do they listen?) Go to the Safari menu (up there, by the Apple icon) and select “Preferences…” then select the “General” tab. Now, look at the bottom:
That checkbox labelled “Open safe files after downloading” should be unchecked, off, not enabled. Do that now.
The second thing? Learn to be cautious. If something starts screaming at you to panic, don’t; calm down and check. If in doubt, don’t install anything. If anything prompts you for your password, make sure you know exactly what it is before typing it in. Your password should only be needed for things you have actively chosen to do.
If you’ve found yourself stuck with one of these pieces of malware, don’t worry: it’s quite easy to remove. Here are instructions for removing several variants of Mac Defender and Mac Protector on the Apple Support Communities forums.
Finally: it may be time to stop sneering at Windows users and accept that anti-malware software could be a good idea. Mark Allan’s ClamXav is free, and can deal with both Mac Defender and Mac Protector. If it saves your bacon, you may want to give Mark a donation via the PayPal link on his site.
Let’s be careful out there, everybody. Oh, and lose the attitude: Windows security is actually pretty good these days. From now on, Macs are only safer if their users are smarter.